SPIP 4.3.3 — Malicious File Upload (XSS in PDF) (CVE-2024–53619)
Description:
We have identified a vulnerability that allows an authenticated admin account to upload a PDF file containing malicious javascript code (Stored Cross-Site Scripting) into the target system. If the file is accessed through the website, it could lead to a Cross-Site Scripting (XSS) attack or execute arbitrary code via a crafted javascript to the target.
Payload:
<script>alert(/Grim The Ripper Team by SOSECURE Thailand/)</script>Affected Component :
http://IP/ecrire/?exec=documents
Proof of Concept:
First, login to the target application.
We login to the target application with admin privileges.
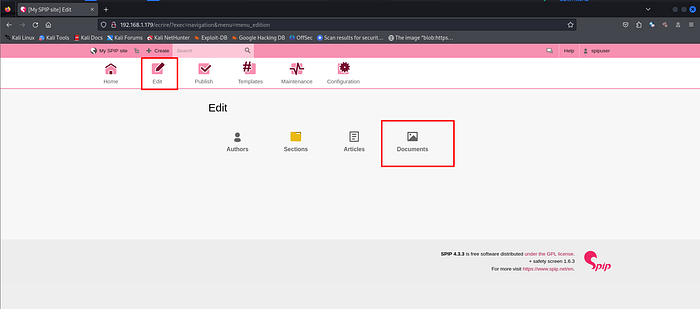
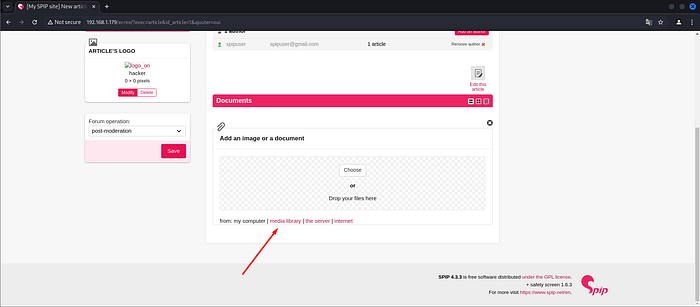
Begin by clicking on the “Edit” tab and click on the “Documents”
Clicking on “Add an image or a document”.
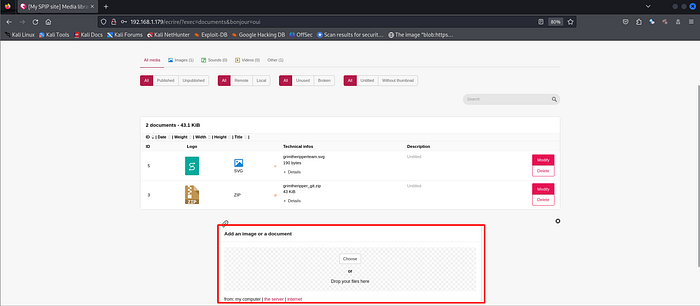
Select the file containing the XSS script that you want to upload.

Click “Open Link in New Tab” in google chrome.
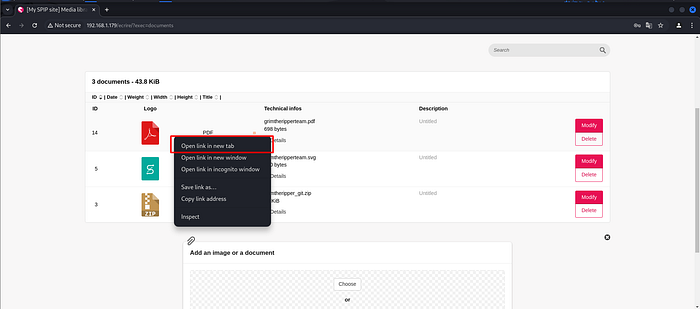
Then clicking change.

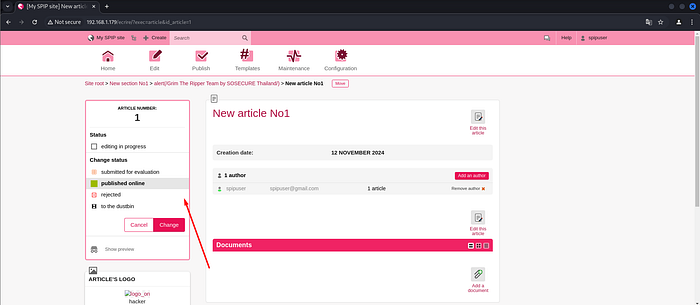
Clicking published online and change.
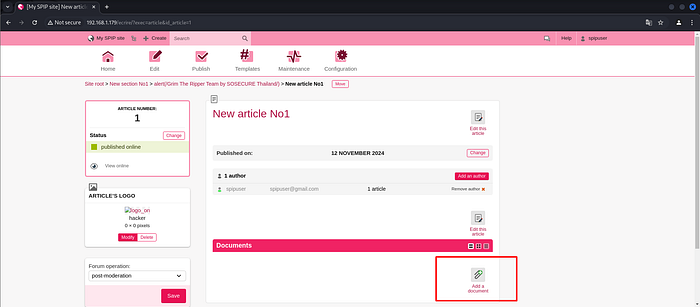
Clicking Add a document.
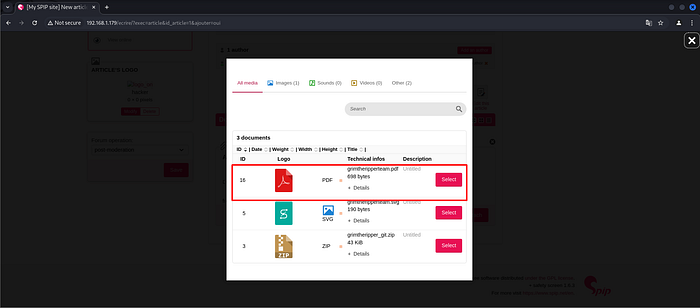
Clicking media library
Clicking Browse…

Select PDF.
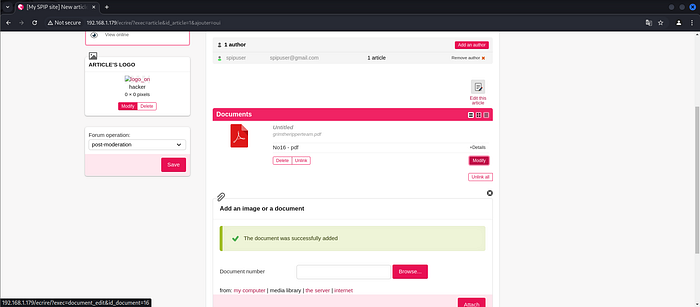
Then go to
http://IP/ecrire/?exec=article&id_article=1

Clicking Open link in new tap.

The XSS payload will run immediately.

Author:
Grim The Ripper Team by SOSECURE Thailand.